We have all received that email that is too good to be true.
“Click here to claim your prize!”
Or the suspicious note from a “friend” asking for help with an unusual task, like paying a stranger, or sending a password.
Such techniques are examples of phishing, where impersonators or fraud actors deceive a victim into revealing personal information, often banking or payment credentials. These can be mistakenly provided by the victim, or accessed through malicious software lurking on the websites that victims are lured to visit.
Phishing may appear innocuous but they can leave lasting damage. The goal of phishing attacks is often to make money.
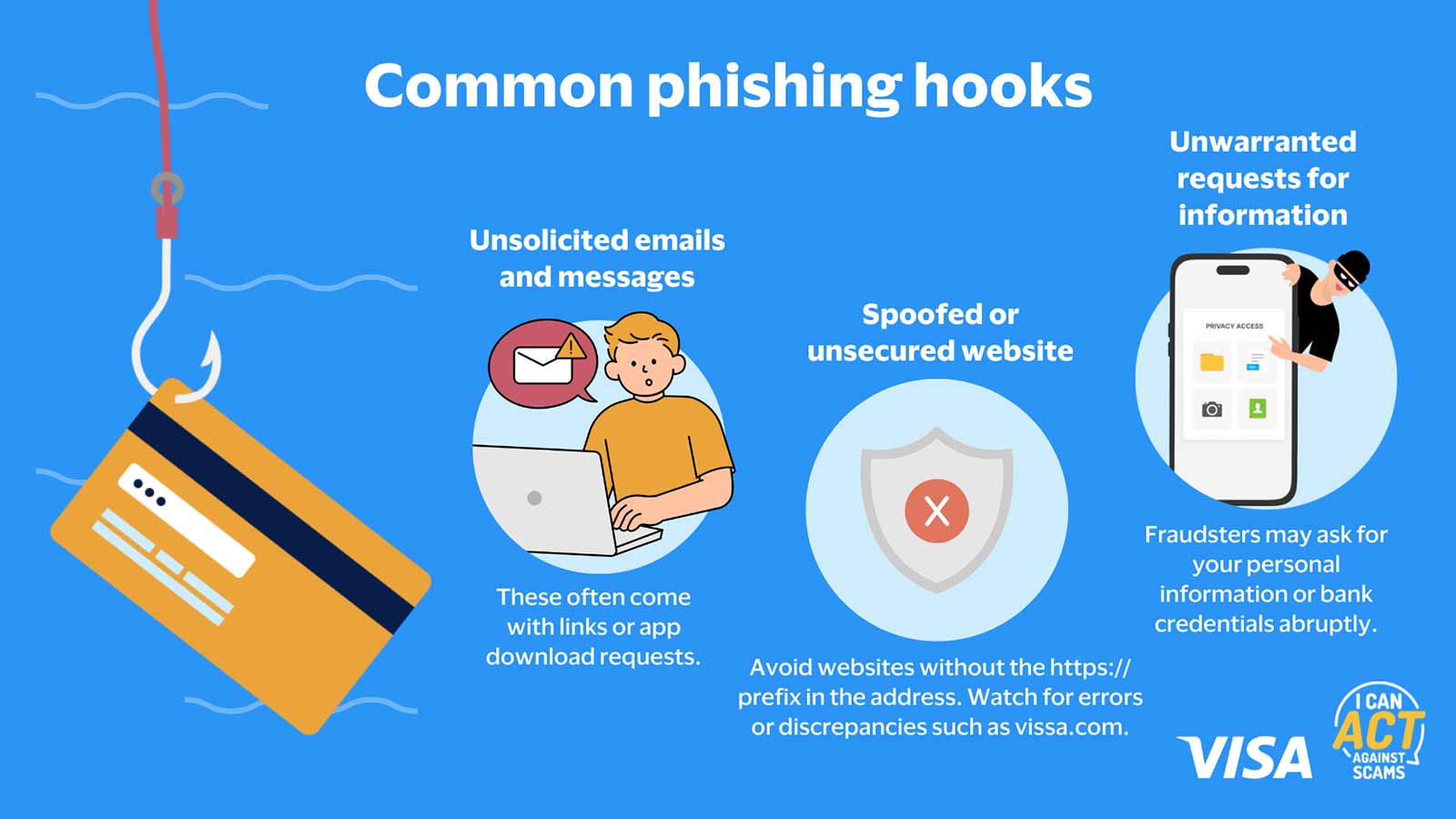
The many faces of phishing
There are many forms of phishing. Some are "spray and pray": large-scale attacks sent to large databases, featuring hundreds of thousands of email addresses, typically acquired illicitly. These aren’t targeting you, but your email address is in that database.
Then there’s spear phishing: personalised emails asking you to do something suspicious for a person or company you know. One variant, whaling, aims to fool high-income or wealthy targets to make fraudulent payments or disclose sensitive data. There’s also pharming, which redirects users from legitimate websites to lookalikes. When victims are prompted to enter their login credentials, they are captured by malware installed on these fake websites.
Beyond links and attachments, fraudsters are fast turning to more sophisticated methods to entrap their victims. Some of them include:
- Clone Phishing: Fraudsters can impersonate a legitimate email with valid links or attachments, replacing them with malicious ones.
- Calendar Phishing: Fraudsters may send calendar invites equipped with malware to access company networks and sensitive information contained within.
- Link Manipulation: Perpetrators create a URL that looks real but actually takes you to a harmful They may also hide or misspell malicious URLs.
More recently, perpetrators have even turned to chatbots and large language models to make conversations more real and believable, making them harder to detect.
How you can stop phishing in its tracks

A combination of vigilance and robust technology can help you spot and stop attacks. Phishing attacks usually involve several common traits. They often request login details and payment information, demand urgent action, or contain suspicious attachments and URLs.
It pays to stay alert when you receive these requests or messages. Here are useful tips you can abide by:
- Pause: Don’t rush. Be mindful of what you are being asked to do to avoid unintentionally clicking on malicious links or entering your private information on unsafe websites. One important tip is to check URLs carefully - scammers often create web addresses that look almost identical to trusted brands or platforms, often with slight differences.
- Check: Always verify that the sender’s identities are legitimate and authentic. Be more cautious about deals that seem too attractive – if the price looks too good to be true, it likely is. If you are still unsure, a quick online search can often tell you whether the image has appeared on another site.
- Ask around: A good way to verify a merchant’s legitimacy is by simply asking your friends and families or looking at customer reviews. Scammers often don’t have many reviews, and the ones they do are overly positive or exaggerated, which is likely a sign they’ve written them themselves.
- Act only when you are sure: Only click on links and provide your personal information when you are certain that they are safe to interact with. Remember that legitimate websites and platforms often accept payments via trusted payment gateways like Visa, which offer additional security capabilities that help to detect and pre-empt fraudulent transactions.
Fortunately, there is also technology on our side. Anti-phishing software are often built into popular email services, which automatically classifies emails with blacklisted domain names as spam. When you are asked to make payment or share banking or card credentials, you can also look out for trusted payment networks like Visa to navigate the online world with more peace of mind.
___________________________________________
¹ Visa, 2024 Global eCommerce Payments & Fraud Report, 25th Edition